Authentication and Security
## Overview {: #overview } The PMF security framework is based on the [OAuth 2.0](http://oauth.net/) protocol. According to this protocol, a resource can be protected by a **scope** that defines the required permissions for accessing the resource. To access a protected resource, the client must provide a matching **access token**, which encapsulates the scope of the authorization that is granted to the client. The OAuth protocol separates the roles of the authorization server and the resource server on which the resource is hosted. * The authorization server manages the client authorization and token generation. * The resource server uses the authorization server to validate the access token that is provided by the client, and ensure that it matches the protecting scope of the requested resource. The security framework is built around an authorization server that implements the OAuth protocol, and exposes the OAuth endpoints with which the client interacts to obtain access tokens. The security framework provides the building blocks for implementing a custom authorization logic on top of the authorization server and the underlying OAuth protocol. By default, PMF functions also as the **authorization server**. The client application can then use these tokens to access resources on a **resource server**, which can be either the PMF itself or an external server. The resource server checks the validity of the token to make sure that the client can be granted access to the requested resource. The separation between resource server and authorization server allows you to enforce security on resources that are running outside PMF. Application developers protect access to their resources by defining the required scope for each protected resource, and implementing **security checks** and **challenge handlers**. The server-side security framework and the client-side API handle the OAuth message exchange and the interaction with the authorization server transparently, allowing developers to focus only on the authorization logic. #### Jump to: {: #jump-to } * [Authorization entities](#authorization-entities) * [Protecting resources](#protecting-resources) * [Authorization flow](#authorization-flow) * [Tutorials to follow next](#tutorials-to-follow-next) ## Authorization entities {: #authorization-entities } ### Access Tokens {: #access-tokens } A PMF access token is a digitally signed entity that describes the authorization permissions of a client. After the client's authorization request for a specific scope is granted, and the client is authenticated, the authorization server's token endpoint sends the client an HTTP response that contains the requested access token. #### Structure {: #structure } The PMF access token contains the following information: * **Client ID**: a unique identifier of the client. * **Scope**: the scope for which the token was granted (see OAuth scopes). This scope does not include the [mandatory application scope](#mandatory-application-scope). * **Token-expiration time**: the time at which the token becomes invalid (expires), in seconds. #### Token expiration {: #token-expiration } The granted access token remains valid until its expiration time elapses. The access token's expiration time is set to the shortest expiration time from among the expiration times of all the security checks in the scope. But if the period until the shortest expiration time is longer than the application's maximum token-expiration period, the token's expiration time is set to the current time plus the maximum expiration period. The default maximum token-expiration period (validity duration) is 3,600 seconds (1 hour), but it can be configured by setting the value of the `maxTokenExpiration` property. See Configuring the maximum access-token expiration period.Configure the application’s maximum access-token expiration period by using one of the following alternative methods:
- Using the PMF Operations Console
- Select [your application] → Security tab.
- In the Token Configuration section, set the value of the Maximum Token-Expiration Period (seconds) field to your preferred value, and click Save. You can repeat this procedure, at any time, to change the maximum token-expiration period, or select Restore Default Values to restore the default value.
- Editing the application's configuration file
- From a command-line window, navigate to the project's root folder and run the
pmfdev app pull. - Open the configuration file, located in the [project-folder]\pmf folder.
- Edit the file by defining a
maxTokenExpirationproperty and set its value to the maximum access-token expiration period, in seconds:{ ... "maxTokenExpiration": 7200 } - Deploy the updated configuration JSON file by running the command:
pmfdev app push.
- From a command-line window, navigate to the project's root folder and run the
Close section
A successful HTTP response to an access-token request contains a JSON object with the access token and additional data. Following is an example of a valid-token response from the authorization server:
HTTP/1.1 200 OK
Content-Type: application/json
Cache-Control: no-store
Pragma: no-cache
{
"token_type": "Bearer",
"expires_in": 3600,
"access_token": "yI6ICJodHRwOi8vc2VydmVyLmV4YW1",
"scope": "scopeElement1 scopeElement2"
}The token-response JSON object has these property objects:
- token_type: the token type is always "Bearer", in accordance with the OAuth 2.0 Bearer Token Usage specification.
- expires_in: the expiration time of the access token, in seconds.
- access_token: the generated access token (actual access tokens are longer than shown in the example).
- scope: the requested scope.
The expires_in and scope information is also contained within the token itself (access_token).
Note: The structure of a valid access-token response is relevant if you use the low-levelWLAuthorizationManagerclass and manage the OAuth interaction between the client and the authorization and resource servers yourself, or if you use a confidential client. If you are using the high-levelWLResourceRequestclass, which encapsulates the OAuth flow for accessing protected resources, the security framework handles the Confidential clients.
Close section
Refresh token feature can be enabled using the following properties on client side and server side respectively.
Client side property (Android)File name: mfpclient.properties
Property name: wlEnableRefreshToken
Property value: true
For example,
wlEnableRefreshToken=true
Client side property (iOS)
File name: mfpclient.plist
Property name: wlEnableRefreshToken
Property value: true
For example,
wlEnableRefreshToken=true
server-side property
File name: server.xml
Property name: mfp.security.refreshtoken.enabled.apps
Property value: application bundle id separated by ‘;’
For example,
<jndiEntry jndiName="mfp/mfp.security.refreshtoken.enabled.apps" value='"com.sample.android.myapp1;com.sample.android.myapp2"'/>
Use different bundle ids for different platforms.
Close section
Following is an example of a valid refresh token response from the authorization server:
HTTP/1.1 200 OK
Content-Type: application/json
Cache-Control: no-store
Pragma: no-cache
{
"token_type": "Bearer",
"expires_in": 3600,
"access_token": "yI6ICJodHRwOi8vc2VydmVyLmV4YW1",
"scope": "scopeElement1 scopeElement2",
"refresh_token": "yI7ICasdsdJodHRwOi8vc2Vashnneh "
}
The refresh-token response has the additional property object refresh_token apart from the other property objects explained as part of the access token response structure.
Close section
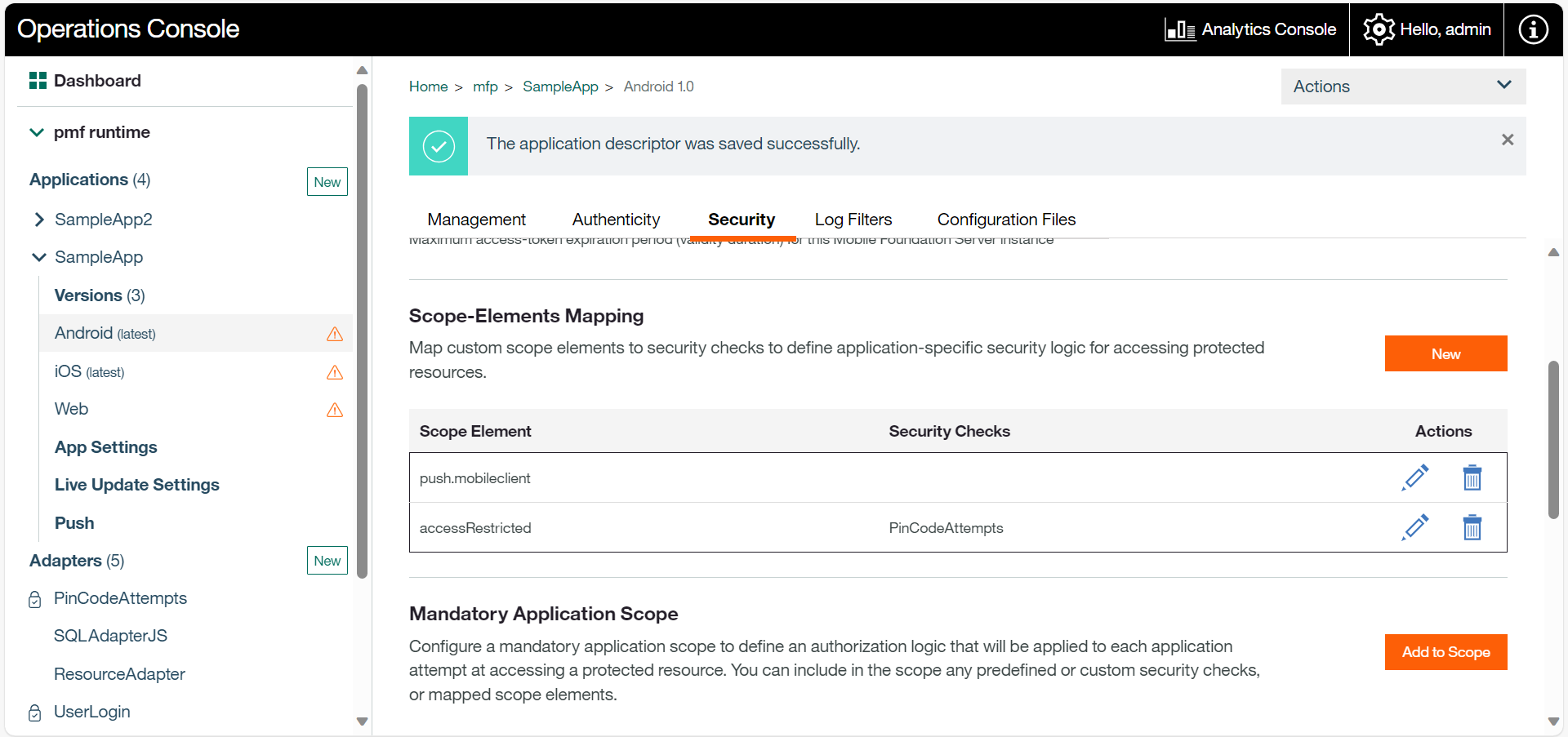 You can also manually edit the application's configuration JSON file with the required configuration and push the changes back to a PMF.
1. From a **command-line window**, navigate to the project's root folder and run the `pmfdev app pull`.
2. Open the configuration file, located in the **[project-folder]\pmf** folder.
3. Edit the file by defining a `scopeElementMapping` property, in this property, define data pairs that are each composed of the name of your selected scope element, and a string of zero or more space-separated security checks to which the element maps. For example:
```xml
"scopeElementMapping": {
"UserAuth": "UserAuthentication",
"SSOUserValidation": "LtpaBasedSSO CredentialsValidation"
}
```
4. Deploy the updated configuration JSON file by running the command: `pmfdev app push`.
> You can also push updated configurations to remote servers. Review the [Using PMF CLI to Manage PMF artifacts](../../application-development/using-mobilefirst-cli-to-manage-mobilefirst-artifacts) tutorial.
## Protecting resources
{: #protecting-resources }
In the OAuth model, a protected resource is a resource that requires an access token. You can use the PMF security framework to protect both resources that are hosted on an instance of PMF, and resources on an external server. You protect a resource by assigning it a scope that defines the required permissions for acquiring an access token for the resource.
You can protect your resources in various ways:
### Mandatory application scope
{: #mandatory-application-scope }
At the application level, you can define a scope that will apply to all the resources used by the application. The security framework runs these checks (if exist) in addition to the security checks of the requested resource scope.
**Note:**
* The mandatory application scope is not applied when accessing [an unprotected resource](#unprotected-resources).
* The access token that is granted for the resource scope does not contain the mandatory application scope.
You can also manually edit the application's configuration JSON file with the required configuration and push the changes back to a PMF.
1. From a **command-line window**, navigate to the project's root folder and run the `pmfdev app pull`.
2. Open the configuration file, located in the **[project-folder]\pmf** folder.
3. Edit the file by defining a `scopeElementMapping` property, in this property, define data pairs that are each composed of the name of your selected scope element, and a string of zero or more space-separated security checks to which the element maps. For example:
```xml
"scopeElementMapping": {
"UserAuth": "UserAuthentication",
"SSOUserValidation": "LtpaBasedSSO CredentialsValidation"
}
```
4. Deploy the updated configuration JSON file by running the command: `pmfdev app push`.
> You can also push updated configurations to remote servers. Review the [Using PMF CLI to Manage PMF artifacts](../../application-development/using-mobilefirst-cli-to-manage-mobilefirst-artifacts) tutorial.
## Protecting resources
{: #protecting-resources }
In the OAuth model, a protected resource is a resource that requires an access token. You can use the PMF security framework to protect both resources that are hosted on an instance of PMF, and resources on an external server. You protect a resource by assigning it a scope that defines the required permissions for acquiring an access token for the resource.
You can protect your resources in various ways:
### Mandatory application scope
{: #mandatory-application-scope }
At the application level, you can define a scope that will apply to all the resources used by the application. The security framework runs these checks (if exist) in addition to the security checks of the requested resource scope.
**Note:**
* The mandatory application scope is not applied when accessing [an unprotected resource](#unprotected-resources).
* The access token that is granted for the resource scope does not contain the mandatory application scope.
In the PMF Operations Console, select your application from the **Applications** section of the navigation sidebar, and then select the **Security** tab. Under **Mandatory Application Scope**, select **Add to Scope**.
 You can also manually edit the application's configuration JSON file with the required configuration and push the changes back to a PMF.
1. From a **command-line window**, navigate to the project's root folder and run the `pmfdev app pull`.
2. Open the configuration file, located in the **project-folder\pmf** folder.
3. Edit the file by defining a `mandatoryScope` property, and setting the property value to a scope string that contains a space-separated list of your selected scope elements. For example:
```xml
"mandatoryScope": "appAuthenticity PincodeValidation"
```
4. Deploy the updated configuration JSON file by running the command: `pmfdev app push`.
> You can also push updated configurations to remote servers. Review the [Using PMF CLI to Manage PMF artifacts](../../application-development/using-mobilefirst-cli-to-manage-mobilefirst-artifacts) tutorial.
### Protecting adapter resources
{: #protecting-adapter-resources }
In your adapter, you can specify the protecting scope for a Java method or JavaScript resource procedure, or for an entire Java resource class, as outlined in the following [Java](#protecting-java-adapter-resources) and [JavaScript](#protecting-javascript-adapter-resources) sections. A scope is defined as a string of one or more space-separated scope elements ("scopeElement1 scopeElement2 ..."), or null to apply the default scope (see [Scopes](#scopes)).
The default PMF scope is `RegisteredClient`, which require an access token for accessing the resource and verifies that the resource request is from an application that is registered with PMF. This protection is always applied, unless you [disable resource protection](#disabling-resource-protection). Therefore, even if you do not set a scope for your resource, it is still protected.
> Note: `RegisteredClient` is a reserved PMF keyword. Do not define custom scope elements or security checks by this name.
#### Protecting Java adapter resources
{: #protecting-java-adapter-resources }
To assign a protecting scope to a JAX-RS method or class, add the `@OAuthSecurity` annotation to the method or class declaration, and set the `scope` element of the annotation to your preferred scope. Replace `YOUR_SCOPE` with a string of one or more scope elements ("scopeElement1 scopeElement2 ..."):
```
@OAuthSecurity(scope = "YOUR_SCOPE")
```
A class scope applies to all of the methods in the class, except for methods that have their own `@OAuthSecurity` annotation.
Note: When the `enabled` element of the `@OAuthSecurity` annotation is set to `false`, the `scope` element is ignored. See [Disabling Java resource protection](#disabling-java-resource-protection).
##### Examples
{: #java-adapter-resource-protection-examples }
The following code protects a `helloUser` method with a scope that contains `UserAuthentication` and `Pincode` scope elements:
```java
@GET
@Path("/{username}")
@OAuthSecurity(scope = "UserAuthentication Pincode")
public String helloUser(@PathParam("username") String name){
...
}
```
The following code protects a `WebSphereResources` class with the predefined `LtpaBasedSSO` security check:
```java
@Path("/users")
@OAuthSecurity(scope = "LtpaBasedSSO")
public class WebSphereResources {
...
}
```
#### Protecting JavaScript adapter resources
{: #protecting-javascript-adapter-resources }
To assign a protecting scope to a JavaScript procedure, in the adapter.xml file, set the scope attribute of the <procedure> element to your preferred scope. Replace `PROCEDURE_NANE` with the name of your procedure, and `YOUR SCOPE` with a string of one or more scope elements ("scopeElement1 scopeElement2 ..."):
```xml
You can also manually edit the application's configuration JSON file with the required configuration and push the changes back to a PMF.
1. From a **command-line window**, navigate to the project's root folder and run the `pmfdev app pull`.
2. Open the configuration file, located in the **project-folder\pmf** folder.
3. Edit the file by defining a `mandatoryScope` property, and setting the property value to a scope string that contains a space-separated list of your selected scope elements. For example:
```xml
"mandatoryScope": "appAuthenticity PincodeValidation"
```
4. Deploy the updated configuration JSON file by running the command: `pmfdev app push`.
> You can also push updated configurations to remote servers. Review the [Using PMF CLI to Manage PMF artifacts](../../application-development/using-mobilefirst-cli-to-manage-mobilefirst-artifacts) tutorial.
### Protecting adapter resources
{: #protecting-adapter-resources }
In your adapter, you can specify the protecting scope for a Java method or JavaScript resource procedure, or for an entire Java resource class, as outlined in the following [Java](#protecting-java-adapter-resources) and [JavaScript](#protecting-javascript-adapter-resources) sections. A scope is defined as a string of one or more space-separated scope elements ("scopeElement1 scopeElement2 ..."), or null to apply the default scope (see [Scopes](#scopes)).
The default PMF scope is `RegisteredClient`, which require an access token for accessing the resource and verifies that the resource request is from an application that is registered with PMF. This protection is always applied, unless you [disable resource protection](#disabling-resource-protection). Therefore, even if you do not set a scope for your resource, it is still protected.
> Note: `RegisteredClient` is a reserved PMF keyword. Do not define custom scope elements or security checks by this name.
#### Protecting Java adapter resources
{: #protecting-java-adapter-resources }
To assign a protecting scope to a JAX-RS method or class, add the `@OAuthSecurity` annotation to the method or class declaration, and set the `scope` element of the annotation to your preferred scope. Replace `YOUR_SCOPE` with a string of one or more scope elements ("scopeElement1 scopeElement2 ..."):
```
@OAuthSecurity(scope = "YOUR_SCOPE")
```
A class scope applies to all of the methods in the class, except for methods that have their own `@OAuthSecurity` annotation.
Note: When the `enabled` element of the `@OAuthSecurity` annotation is set to `false`, the `scope` element is ignored. See [Disabling Java resource protection](#disabling-java-resource-protection).
##### Examples
{: #java-adapter-resource-protection-examples }
The following code protects a `helloUser` method with a scope that contains `UserAuthentication` and `Pincode` scope elements:
```java
@GET
@Path("/{username}")
@OAuthSecurity(scope = "UserAuthentication Pincode")
public String helloUser(@PathParam("username") String name){
...
}
```
The following code protects a `WebSphereResources` class with the predefined `LtpaBasedSSO` security check:
```java
@Path("/users")
@OAuthSecurity(scope = "LtpaBasedSSO")
public class WebSphereResources {
...
}
```
#### Protecting JavaScript adapter resources
{: #protecting-javascript-adapter-resources }
To assign a protecting scope to a JavaScript procedure, in the adapter.xml file, set the scope attribute of the <procedure> element to your preferred scope. Replace `PROCEDURE_NANE` with the name of your procedure, and `YOUR SCOPE` with a string of one or more scope elements ("scopeElement1 scopeElement2 ..."):
```xml